Galileo Open Service Message Authentication (OSNMA) vs. dual antenna receivers to detect GNSS spoofing / ION-ITM 2024
23 January 2024
The proliferation of counterfeit GNSS signals is increasingly posing a significant challenge (source: https://www.reuters.com/business/aerospace-defense/airline-industry-meet-january-over-gps-spoofing-spike-2023-12-06/). Our research, showcased at the ION ITM 2024 conference (program details: https://www.ion.org/itm/program.cfm), demonstrates through real-world spoofing attacks that the combination of Galileo OSNMA and a dual-antenna receiver synergize effectively, facilitating robust and swift detection of spoofing attacks.
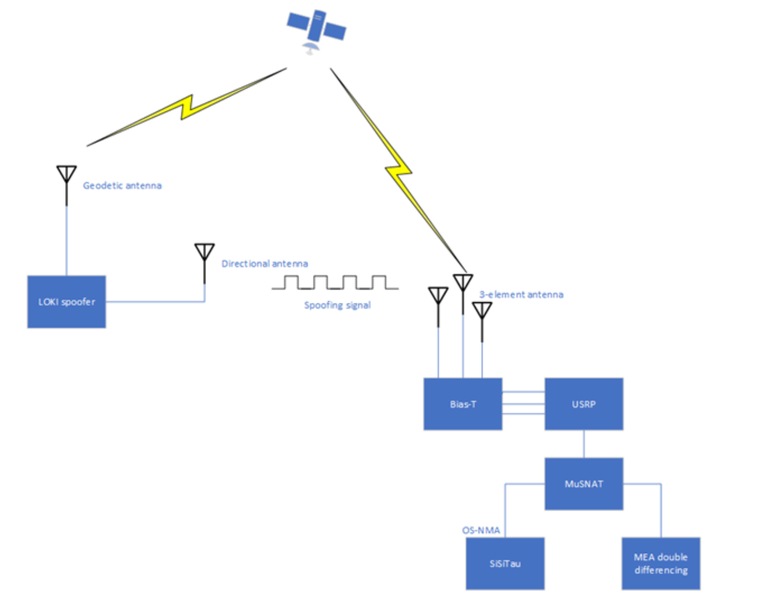
Overall set-up of the spoofing scenario comprised for the spoofing set-up, a geodetic receiving multi element antenna (MEA) under spoofing attack and the commercial spoofing and jamming device including a directional transmitting antenna pointing towards the antenna of the receiver to be spoofed. For the receiver to be spoofed two elements of a multi-element antenna and a USRP 2955 with synchronized clocks has been used. The signal processing of the Galileo E1-B/C and the GPS L1C/A has been done by using the MuSNAT software receiver (https://www.unibw.de/lrt9/lrt-9.2/software-packages/musnat), with master-slaving tracking architecture, i.e. the master channels controls the numerically controlled oscillators (NCO) of the slave channels.
The figures below show the physical setup and a block diagram. Signal power was chosen properly so that spoofing signal power is below reception level outside the University campus. Furthermore, the spoofing is fine-tuned so that obvious metrics like signal power or time jumps are not available to the victim user to detect spoofing.


The spoofing procedure was the following: first 5.6 minutes of spoofer initialization without transmitting, then the spoofing transmission was activated, and it run for 8 minutes, then the spoofer was disabled, and the real signal was received for another 5 minutes approximately.
By using the output of the master Galileo channels, the Galileo OSNMA bits have been processed, and the results shown in the figure below have been obtained. Blue and turquoise dots indicate data availability and magenta indicates that OSNMA verified a signal to be authentic. On the other hand, orange dots indicate that spoofing was detected for four received Galileo signals. PRN 15 and 27 were never successfully spoofed, and only the authentic signals are tracked during the complete test. PRN 13 and 21 however, were successfully spoofed. PRN 30 and 34 are only visible during the spoofing period because during the real-signal-only periods, the signals are blocked for the victim receiver, but not for the spoofer, therefore, it retransmits those PRNs during the spoofing period.


Two receive antennas allow to estimate the direction of arrival of a GNSS signal. If two signals originate from the very same direction, then this can be seen as a spoofing indicator. Using the master-slave architecture, double difference phase discriminator values near zero indicate identical direction of arrival. With this methodology spoofing is observed in the last 4 minutes of the spoofing period for all the GPS L1C/A signals and for the spoofed Galileo E1BC signals as shown in the figure below.


We conclude that spoofing effects have a comparable complex signature on victim receivers. Double differenced phase discriminator values almost instantaneously give an indication that a spoofing attack is ongoing but need proper verification with statistical methods. On the other hand, OSNMA has a latency of minimum 30 s but gives a unique indication that spoofing is ongoing. Together they allow fast and reliable spoofing identification.
For more information, please contact markel.arizabaleta@unibw.de