NordSec 2024 - Paper accepted
26 September 2024
Our work in a nutshell:
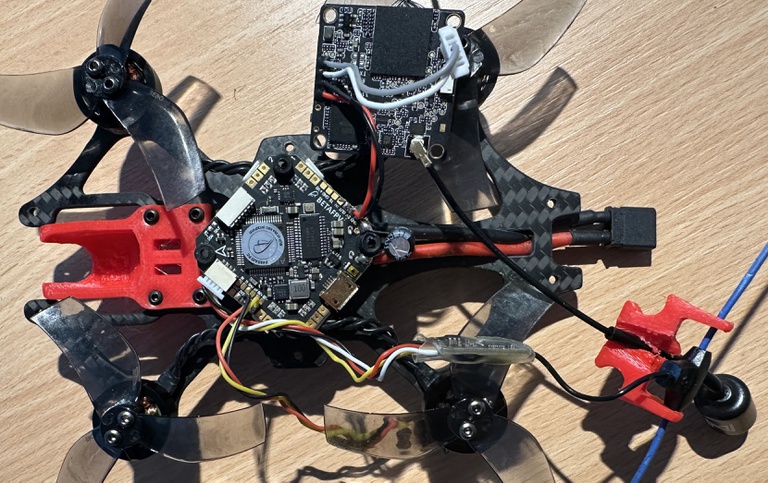
In recent years, Unmanned Aerial Vehicles (UAVs) or drones have gained attention for various applications, with mainstream brands like DJI dominating the civil market. However, DIY drones pose unique challenges due to their use in unconventional and illegal activities, but research into their digital forensic examination remains limited. This paper addresses the gap by conducting a comprehensive case study on a DIY drone, focusing on both assembly and digital forensics, revealing that hardware identification is the most critical step in the examination process.
This work has been developed in the project FOCUS. FOCUS (reference number: 13N16510) is partly funded by the German ministry
of education and research (BMBF) within the research programme “Anwender – Innovativ: Forschung für die zivile Sicherheit II”.

Paper Details:
Title: "Beware of the Rabbit Hole -- A Digital Forensic Case Study of DIY Drones"
Authors: Samantha Klier and Harald Baier
Abstract: In the past years, Unmanned Aerial Vehicles (UAVs), commonly known as drones, have drawn attention for commercial, military and private use and thus emerged as a significant source of digital evidence. As of today both the research community and commercial software manufacturer focus on UAV mainstream brands such as DJI, which holds a market share of roughly 80% of the civil market. On the other side Do-It-Yourself (DIY) drones are well suited for unconventional and illegal
activities due to their technical capabilities and the legal limitations of commercial drones. However, the community currently lacks research of the examination of DIY drones. In this paper we address this research gap by conducting a comprehensive case study of a sample DIY drone. Our case study comprises both the assembly and the digital forensic perspective of DIY drones. Our systematic digital forensic examination within our case study follows the well-known process steps, i.e. preparation, acquisition, analysis. We provide insights into the peculiarities of each step and reveal that the identification of the hardware components
and the corresponding examination is the most critical step.





